Instant messaging (IM) has become a very popular medium for communicating over the Internet. With so many available services like MSN Messenger, Yahoo! Messenger, and AOL Instant Messenger, it is no wonder why so many people are flocking to use the free software. Don’t think that it’s just teenagers and their friends using IM services either. Hackers and other would-be computer intruders are now using IM as a way to put viruses, worms, spyware, and other types of malicious software on your computer. In fact, IM is catching up to e-mail as one of the main sources of malicious computer attacks.
Contrary to popular belief, most IM programs are not very secure. They were not originally designed with all of the security features that come with other types of communication programs (e.g., email). Due to the initial lack of security, it is very easy for hackers to slip a fake link or virus into an instant message. While most IM companies have been addressing security flaws with their software, some individual users don’t update the software or follow the necessary steps to keep their IM software safe.
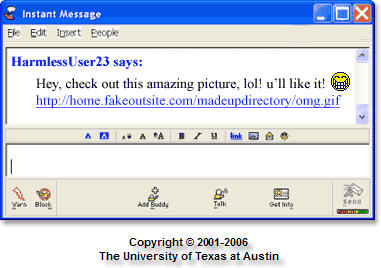
College campuses have long been a popular place for IM. As such, university computer staffs around the United States have become involved in combating the security woes of IM. The University of Texas at Austin, for example, regularly updates students about the security dangers of IM and what they can do to protect their personal information. The screenshot below, from the University of Texas, shows an example of a fake instant message that contains a bogus link.
I want to pass on four ideas that the Information and Technology Services team at the University of Texas put together to help students, parents, and anyone who uses IM regularly. You can find the full article on the ITS page at the University of Texas.
Keep your IM password safe. Use a difficult to guess password (lots of random letters, numbers, and characters) and don’t let the IM program “remember” your password or sign you in automatically to your account.
Watch incoming messages or file transfers. Unless you are expecting a message or file transfer, don’t accept it. This is tricky because IM screen names are very easy for hackers to get a hold of and use. So you may receive a link from a screen name that is listed in your buddy list, but the link is bogus (see screenshot above).
Limit the use of personal and confidential information. IM conversations are often not private or encrypted, which means they are not changed so it becomes difficult for others to read them. If you really need to give out personal information to someone via IM, I recommend using another secure communication medium such as landline telephone or encrypted email.
Download security upgrades. Use automatic updates or regularly check your IM software company’s Web site for updates. IM companies are becoming more active in keeping their software secure.

